Let's Encrypt提供了免费的SSL证书申请,域名个数不限,一次申请成功后有效期为3个月。可以无限续命。WinACME提供了在Windows环境下Let's Encrypt证书的申请、部署和续命功能,并且对IIS非常友好。
命令行运行,显示
[INFO] A Simple ACME Client for Windows (WACS)
[INFO] Software version 1911.2.6726.40690 (RELEASE)
[INFO] IIS version 8.5
[INFO] ACME server https://acme-v01.api.letsencrypt.org/
[INFO] Please report issues at https://github.com/PKISharp/win-acme
N: Create new certificate
M: Create new certificate with advanced options
L: List scheduled renewals
R: Renew scheduled
S: Renew specific
A: Renew *all*
V: Revoke certificate
C: Cancel scheduled renewal
X: Cancel *all* scheduled renewals
Q: Quit
Please choose from the menu:
其中,N和M选项都可以用来自动创建证书。下面展示一下M选项创建证书的流程,因为这个相对复杂,而N相对而言只是它的简化。
下面我们输入M。
[INFO] Running in Advanced mode
1: Single binding of an IIS site
2: SAN certificate for all bindings of an IIS site
3: SAN certificate for all bindings of multiple IIS sites
4: Manually input host names
C: Cancel
Which kind of certificate would you like to create?:
1、2、3选项的binding和site之间的区别简单地解释一下。site顾名思义指一个IIS站点,而binding指一个站点绑定的“域名:端口”。一个site可以对应一个或多个binding。
下面我们输入3。
[INFO] No valid hosts found for HTTPS.
5: 站点A (1 bindings) [@C:\站点A]
6: 站点B (1 bindings) [@C:\站点B]
2: 站点C (1 bindings) [@C:\站点C]
1: 站点D (2 bindings) [@C:\站点D]
Enter a comma separated list of site IDs, or 'S' to run for all sites:
下面列出了IIS中已经创建的所有站点和binding的数量、站点路径,可以看到一共有4个站点、5个binding。最前面的是站点的编号。这里要求输入要申请证书的站点序号(半角逗号分隔),或者输入S选择所有站点。
下面我们输入S。
* 1.licc.tech
* 2.licc.tech
* 3.licc.tech
* licc.tech
* www.licc.tech
Press enter to include all listed hosts, or type a comma-separated lists of exclusions:
这里显示了所有站点的域名,你可以输入不需要申请证书的域名(半角逗号分隔),或者直接Enter为所有域名申请证书。
下面我们直接Enter。
1: 1.licc.tech
2: 2.licc.tech
3: licc.tech
4: 3.licc.tech
5: www.licc.tech
Choose a domain name to be the certificate's common name:
这里要求选择主域名的序号。所谓的主域名,就是证书颁发对象的名称所显示的域名,如下图所示:
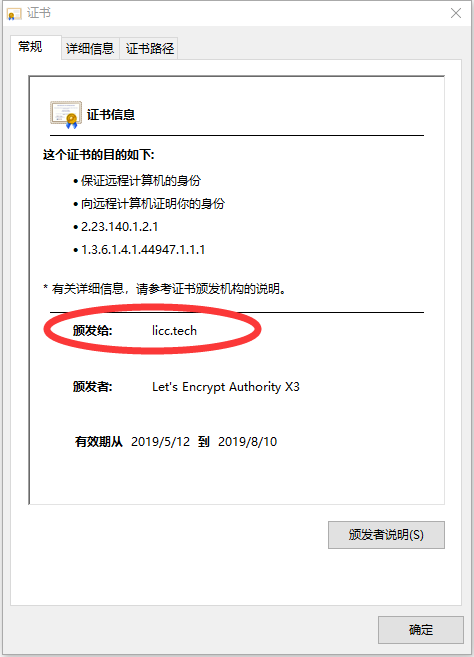
值得注意的是,截至目前版本,N选项自动创建的证书不一定会选择顶级域名作为主域名,而可能选取某个二级域名,使得证书信息很不好看(强迫症使然)。这也是为什么优先介绍M选项的原因之一。
接下来我们输入顶级域名对应的序号3。
[INFO] Plugin IISSites generated target [IISSites] 5,6,2,1 [5 bindings - 1.licc.tech, ...]
1: [dns-01] Azure DNS
2: [dns-01] Run external program/script to create and update records
3: [http-01] Create temporary application in IIS
4: [http-01] Save file on local (network) path
5: [http-01] Self-host verification files (recommended)
6: [http-01] Upload verification file to FTP(S) server
7: [http-01] Upload verification file to WebDav path
C: Cancel
How would you like to validate this certificate?:
这里提供了7种验证上述域名的所有者为你的方法。方法5是最推荐的,对于IIS站点,方法5几乎可以全自动地完成域名验证。
但是对于当前未备案而被接入商拦截了80端口的情形,方法5就不能生效了。这个时候可以采用方法2。方法2需要在你上述每个域名下添加一条TEXT记录来验证,WinACME会调用2个由你提供的程序或批处理,1个用于添加纪录,1个用于验证完成后删除记录。如果你本机开启了DNS服务、域名的NS记录也指向本机,可以利用Add-DnsServerResourceRecord和Remove-DnsServerResourceRecord这两条Powershell来实现记录的增删。具体实现不再赘述,这里着重讲一下推荐的方法5。
下面我们输入5。
1: Create or update https bindings in IIS
2: Do not run any installation steps
3: Run a custom script
C: Cancel
Which installer should run for the certificate?:
下面是证书的安装选项。选择1可以自动将证书设置为相应站点的HTTPS证书。
下面我们输入1。
Would you like to add another installer step? (y/n):
输入n。
Use different site for installation? (y/n):
再次输入n。
[INFO] Authorize identifier: 1.licc.tech
[INFO] Cached authorization result: valid
[INFO] Authorize identifier: 2.licc.tech
[INFO] Cached authorization result: valid
[INFO] Authorize identifier: 3.licc.tech
[INFO] Cached authorization result: valid
[INFO] Authorize identifier: licc.tech
[INFO] Cached authorization result: valid
[INFO] Authorize identifier: www.licc.tech
[INFO] Cached authorization result: valid
[INFO] Requesting certificate 5,6,2,1 2018/7/19 1:54:11 上午
[INFO] Saving certificate to C:\ProgramData\win-acme\httpsacme-v01.api.letsencrypt.org
[INFO] Installing certificate in the certificate store
[INFO] Adding certificate 5,6,2,1 2018/7/19 1:54:11 上午 to store WebHosting
[INFO] Installing with IIS...
[INFO] Updating existing https binding 1.licc.tech:443
[INFO] Committing 1 https binding changes to IIS
[INFO] IIS will serve the new certificates after the Application Pool IdleTimeout has been reached.
[INFO] Updating existing https binding 2.licc.tech:443
[INFO] Committing 1 https binding changes to IIS
[INFO] IIS will serve the new certificates after the Application Pool IdleTimeout has been reached.
[INFO] Updating existing https binding 3.licc.tech:443
[INFO] Committing 1 https binding changes to IIS
[INFO] IIS will serve the new certificates after the Application Pool IdleTimeout has been reached.
[INFO] Updating existing https binding licc.tech:443
[INFO] Updating existing https binding www.licc.tech:443
[INFO] Committing 2 https binding changes to IIS
[INFO] IIS will serve the new certificates after the Application Pool IdleTimeout has been reached.
[INFO] Adding Task Scheduler entry with the following settings
[INFO] - Name win-acme httpsacme-v01.api.letsencrypt.org
[INFO] - Path C:\WinACME
[INFO] - Command letsencrypt.exe --renew --baseuri "https://acme-v01.api.letsencrypt.org/"
[INFO] - Start at 09:00:00
[INFO] - Time limit 02:00:00
Do you want to specify the user the task will run as? (y/n):
这里会展示域名验证的结果,在验证完成后,证书会被安装到对应的IIS站点。同时,程序创建了一个在证书即将到期时更新证书的计划任务。你可以指定运行这个计划任务的用户,但这里我们直接输入n使用当前用户。
输入n。
[INFO] Adding renewal for 5,6,2,1
[INFO] Next renewal scheduled at 2018/9/11 17:54:25 下午
N: Create new certificate
M: Create new certificate with advanced options
L: List scheduled renewals
R: Renew scheduled
S: Renew specific
A: Renew *all*
V: Revoke certificate
C: Cancel scheduled renewal
X: Cancel *all* scheduled renewals
Q: Quit
Please choose from the menu:
至此,证书的申请、安装、自动续命就已全部完成。